Accurate as of 10/26/2023 4:26 pm
The world is a very tumultuous place right now. One constant we can count on is new threats!
This time we are talking about GhostRAT, which (in our found version) was labeled “BlueCheck card secret generation.exe” once translated. Below is the actual file name as the process attempts to start (it’s a simple wrapper that attempts to download additional components).
We did some analysis as it ran looking to see where it was communicating, and we found the following information about the connections –
This is one of the first instances we have found of a dropper communicating back to mainland China to pull the payloads. This signifies a potential shift in targets for Chinese APTs.
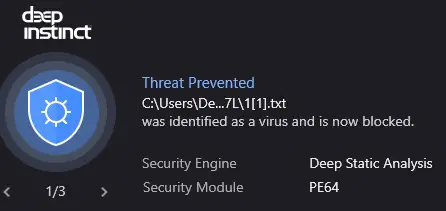
This is a multi-stage payload which attempts to pull down multiple files. The first is a TXT file that is actually an exe file. There is also a second file dropped with the txt file which is a helper file. Our prevention-first solution catches this and shuts it down before it can write to the machine –
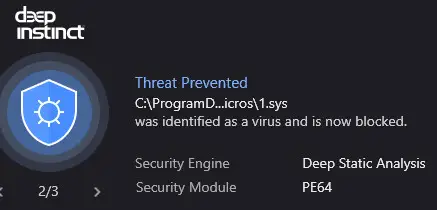
There is also a dropped sys file which helps with enabling the RAT and its functionality. This too is prevented outright by our prevention solution!
Why is this important? At the time of posting this, very few EDRs were able to detect this, and no others prevented the extra payloads such as the sys file.
Please understand this is not to scare anyone but to bring awareness to the constant evolution of threats along with known advanced persistent threats shifting attention to targets outside of large enterprises.