You may be receiving a lot of requests from your customers regarding False Positives in the email filter. You may also be thinking to yourself “Self, it sure does seem like there have been a lot of False Positives Quarantined in my email lately!”.
For many MSPs, the next step is to go to your security provider asking all the “what, why, how questions,” ultimately asking the security provider to fix it. Well, the simple answer yes, we know this is happening. Unfortunately, we the security providers are not able fix it and Microsoft is wholly responsible for the issues that we are seeing!
Algorithm Shift
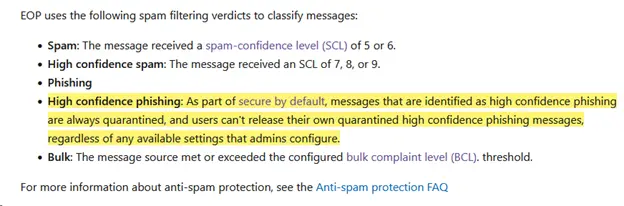
Every couple years, Microsoft tweaks its algorithms for detecting Phishing messages, and it seems to have occurred again with their recent announcement of the “Secure Future Initiative.” This has, in turn, created massive headaches for admins in the world, particularly when considering changes to the High Confidence Phishing Engine.
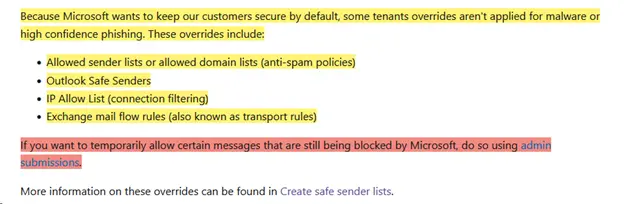
Many may recall that this is not the first time MS has created an administrative nightmare with these shenanigans. A few years back, Microsoft went to a “Secure by Default” Model and created similar issues with many admins flurrying to find a solution or work-around. At the time, Microsoft provided work arounds or solutions in the form of allow-lists or Exchange Mail Flow rules that would preempt the filter. It seems the difference this time is that MS has removed many of these solutions or work arounds and is beginning to force admins to go through MS support for the answer. Of course, MS Support has a stellar track record of making things extremely easy (tongue firmly planted in cheek).
30-Day Email Submission Review
To make things worse, if an administrator is not aware that the email was flagged as High Confidence Phishing by Microsoft, it will sit in the quarantine for 30 days before being permanently deleted from Microsoft’s servers, with no way to recover the message for further analysis.
We have not been able to identify a workaround for this, at this time. We have brought this to our vendor, and they are also seeing many complaints regarding the recent changes. Our product partner has been in contact with Microsoft; however, they have not been able to make much progress in coming up with a solution to this problem.
Next Steps
We recommend all of our MSP partners follow the process laid out by Microsoft but also escalate to the highest levels possible to complain about not being able to perform analysis and allow-listing for your customers.
We will continue to work on getting a solution through our product partners. Hopefully, with some pressure on Microsoft from their customer base, there will be a better solution in the coming months.
Additional References
- https://answers.microsoft.com/en-us/msoffice/forum/all/quarantine-reason-high-confidence-phish/4eeb198f-8d00-43c3-b408-a4bdb430e80c
- https://www.reddit.com/r/Office365/comments/14riq05/microsoft_marking_our_emails_as_high_confidence/
- https://techcommunity.microsoft.com/t5/microsoft-defender-xdr/standard-security-policy-flagging-too-many-emails-as-quot/m-p/3909626