Information Updated as of 3/13/2024 17:48 PDT
DocuSign is being used along with malicious PDF files to spread banking trojans around the world but currently focused on Latin America. This does not mean the bad actors will not decide to start attacking US targets, in fact it’s almost a guarantee a shift will happen and people in the US will start being targeted.
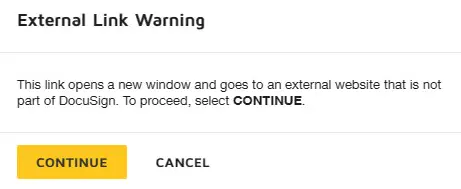
The attack leverages the actual Docusign Portal, but then points to a different website.
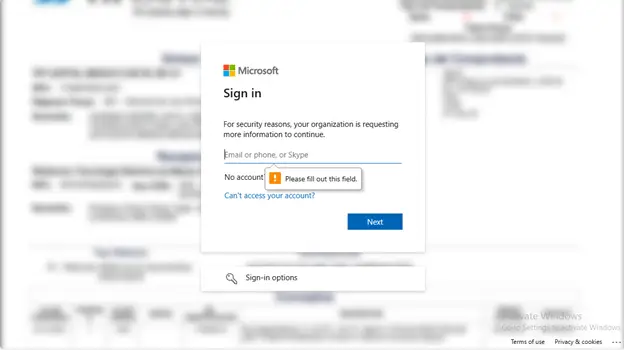
It takes you to a page that looks like you need to login prior to accessing the document, but this website is not actually a MS website –
The attack is attempted via phishing, or, in some cases, the button asking you to sign and complete is a link to download malicious content, specifically a trojan.
These new attacks attempt to leverage “Lightshot” and include a DLL named “Ghostshot” which is installed as a part of a malicious MSI package downloaded by the PDF when you try to “sign and complete” the document. There is also an attempt to download PUA in the form of a RAR package, used in conjunction with the DLL files dropped by Lightshot.
Action Needed: If you receive something from DocuSign, reach out to those who sent it directly before you click on anything to validate it’s a legit document!
NOTE: If you are a BLOKWORX Partner leveraging our SCUD and MAED solutions, you are protected from this attack.