The Silent Security Risk in Your Virtual Meeting

In today’s fast-paced business environment, AI meeting assistants like Microsoft Copilot, Otter.ai, and Fireflies.ai have become increasingly popular tools for capturing and summarizing discussions. These digital scribes promise enhanced productivity, perfect recall, and the elimination of manual note-taking. However, beneath their convenience lies a concerning set of security and compliance risks that many organizations […]
From Fiction to Fact: The Quantum Leap
Have you ever watched a sci-fi movie where the protagonists face an unstoppable technological threat and thought, “glad that’s not real”? Well, the quantum threat is no longer fiction. Microsoft just unveiled their Majorana 1 chip – the first quantum processor using topological qubits. This isn’t just another incremental advance. This architecture could eventually […]
Silent Threats: Why Waiting for Detection Is a Risk You Can’t Afford

Imagine someone sneaking into your house and living in your attic for over six months. They’re not making noise or setting off any alarms—they’re just watching, learning, and waiting for the perfect time to strike. Creepy, right? That’s exactly how many modern cyberattacks unfold. The longer the attacker goes unnoticed, the more damage they […]
The Hidden Cost of Weak Cybersecurity: How Downtime Drains Your Business

Downtime caused by cyberattacks is more than just a temporary inconvenience—it’s a direct hit to your bottom line. Every second of system failure can cost companies thousands, while long-term reputational damage can be devastating. Yet, many businesses underestimate the true financial impact of breaches, downtime, and security failures. This article isn’t meant to […]
Cloud Chaos
In the digital age, businesses heavily rely on cloud services for daily operations. However, recent events, such as the widespread Microsoft 365 outage on March 1, 2025, have highlighted the vulnerabilities inherent in these dependencies. This particular incident left tens of thousands of users unable to access essential services like Outlook, Teams, and Office […]
Cyber Hygiene Matters: The Small Security Steps That Prevent Big Breaches

While cyber hygiene may sound basic, poor security practices continue to be a leading cause of breaches. Weak passwords, outdated software, and insufficient phishing awareness training remain some of the most significantsecurity gaps, leaving organizations vulnerable to cyberattacks.A lack of cyber hygiene is no longer an oversight—it’s an open invitation for attackers. Let’s explore why […]
Into the Deep: The Alarming Risks of Deep Seek

Recent reports have brought Deep Seek into the spotlight, not for its innovations, but for the critical security vulnerabilities it presents. As cybersecurity professionals, it’s essential to stay informed about emerging threats, and Deep Seek has proven to be a potential risk that organizations can’t afford to ignore. The Dangers of Deep Seek Studies […]
TikTok Ban and Data Privacy: Why Americans Are Flocking to Rednote

In recent years, TikTok has faced increasing scrutiny over its data privacy practices, culminating in bans in certain regions of the United States. These actions stem from widespread concerns about data collection, user privacy, and the app’s ties to ByteDance, a company with headquarters in Beijing. However, as TikTok faces these challenges, a surprising trend […]
Data Breach Survival Guide: What Happens Next?
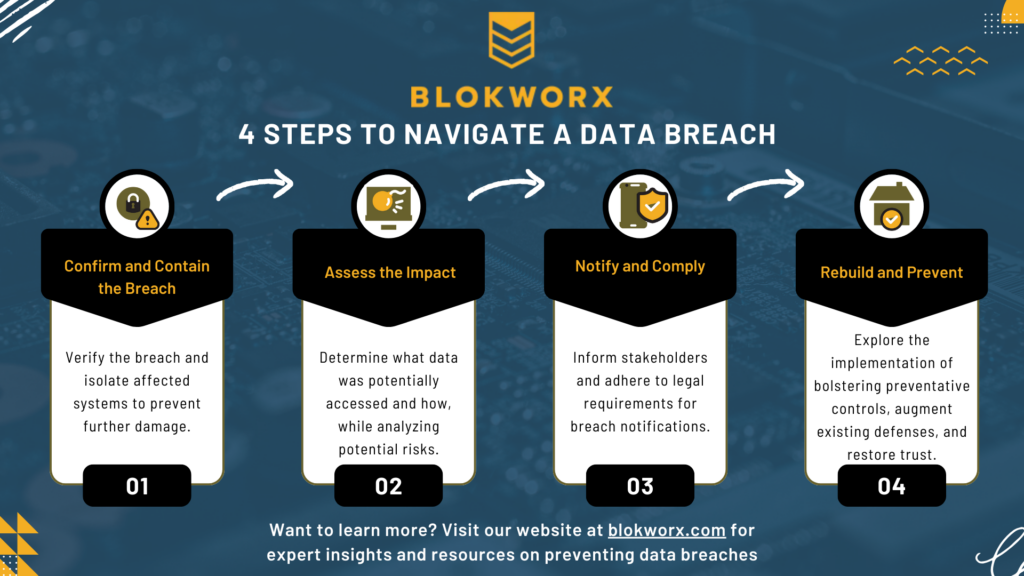
More often than anyone would like, businesses face the unsettling reality of having their sensitive information exposed via a breach. Even more concerning to consumers, these businesses store and retain data belonging to their customers which waterfalls down to not only expose business data, but individual user data as well. But what happens after […]
Getting the Most Out of Your Palo Alto Networks Solution Stack
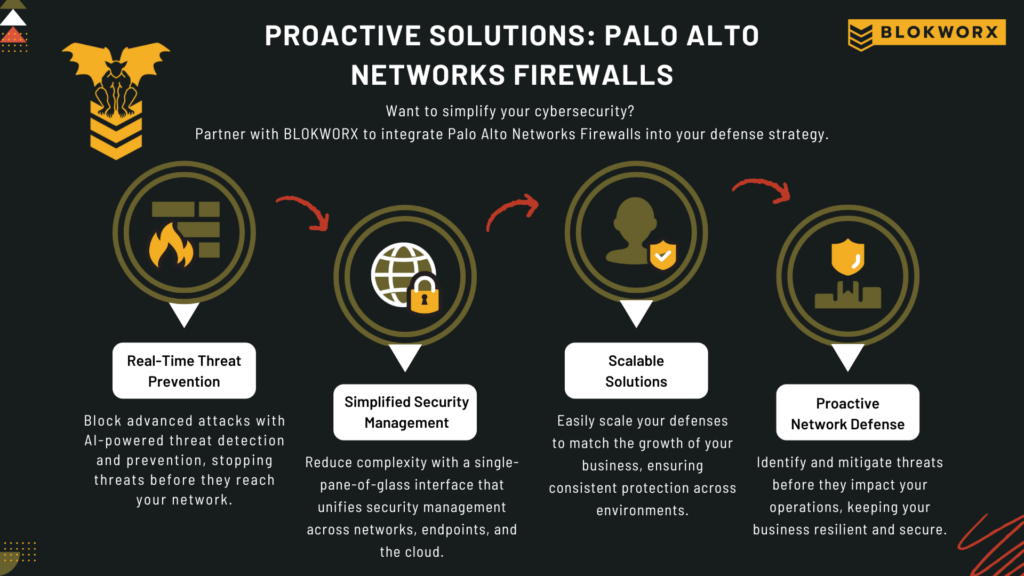
Managing a Palo Alto Networks firewall and ensuring you get every ounce of horsepower out of the feature stack can feel overwhelming. The challenges of implementing seamless SD-WAN, optimizing updates with the latest threat intelligence, or properly configuring the advanced features can result in a lack of certainty, fatigue, or both—but they don’t have to. […]
Cyber Cleanup: Post-Holiday Security Checklist to Start the New Year Right

The holiday season is a time for celebration, giving, and connection. But for cybercriminals, it’s open season for phishing scams, fraudulent transactions, and exploiting new tech gifts. As the festive season winds down, it’s crucial to prepare for the new year with a strong cybersecurity foundation. Use this post-holiday checklist to secure your digital world […]
Unwrap with Care: Holiday Tips for Securing Your New Tech

The holiday season is upon us, and with it comes the excitement of unwrapping shiny new tech gadgets. Whether it’s a sleek smartphone, a cutting-edge smartwatch, or the latest smart home assistant, these devices promise convenience and fun. However, they also introduce new cybersecurity risks that, if ignored, could dampen your holiday cheer. Here’s how […]
