BLOG
In the digital age, businesses heavily rely on cloud services for daily operations. However, recent events, such as the widespread Microsoft 365 outage on March 1, 2025, have highlighted the...
While cyber hygiene may sound basic, poor security practices continue to be a leading cause of breaches. Weak passwords, outdated software, and insufficient phishing awareness training remain some of...
Recent reports have brought Deep Seek into the spotlight, not for its innovations, but for the critical security vulnerabilities it presents. As cybersecurity professionals, it’s...
In recent years, TikTok has faced increasing scrutiny over its data privacy practices, culminating in bans in certain regions of the United States. These actions stem from widespread concerns about...
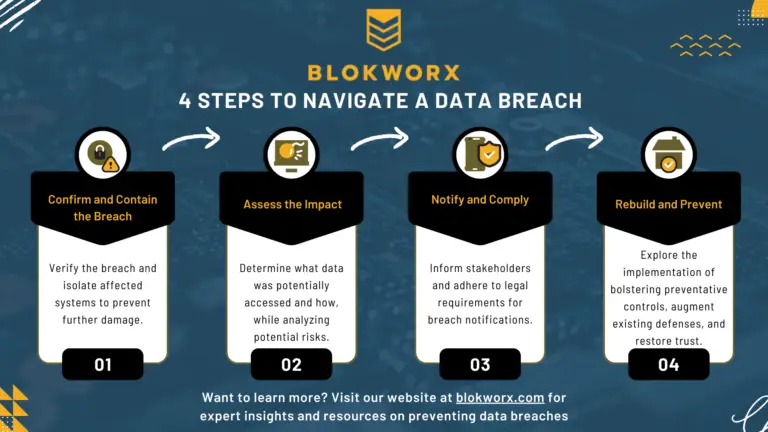
More often than anyone would like, businesses face the unsettling reality of having their sensitive information exposed via a breach. Even more concerning to consumers, these businesses store...
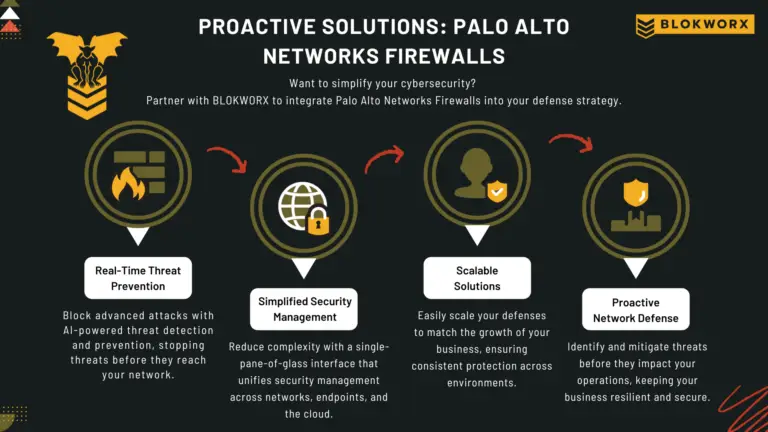
Managing a Palo Alto Networks firewall and ensuring you get every ounce of horsepower out of the feature stack can feel overwhelming. The challenges of implementing seamless SD-WAN, optimizing updates...
The holiday season is a time for celebration, giving, and connection. But for cybercriminals, it’s open season for phishing scams, fraudulent transactions, and exploiting new tech gifts. As the...
The holiday season is upon us, and with it comes the excitement of unwrapping shiny new tech gadgets. Whether it’s a sleek smartphone, a cutting-edge smartwatch, or the latest smart home assistant...
Cyber Monday is a shopper’s paradise, a day of unbeatable deals and exciting discounts. However, it’s also prime time for cybercriminals to strike. As the online shopping frenzy unfolds...