BLOG
In this season of thankfulness, we’re reminded of the vital partnerships that form the backbone of our cybersecurity efforts. In our latest Safety Brief episode, “Thankfulness in Cybersecurity:...
As we wrap up Cybersecurity Awareness Month, let’s look back on October’s initiatives and share how BLOKWORX is committed to fostering cybersecurity awareness year-round. This October, we...
In the dark corners of the internet, a silent army of compromised computers known as botnets or “zombie networks” lurks, waiting to execute the commands of cybercriminals operating...
When disaster strikes, communities come together to rebuild and support each other. Unfortunately, it’s also a time when bad actors take advantage of people’s vulnerabilities. Natural...
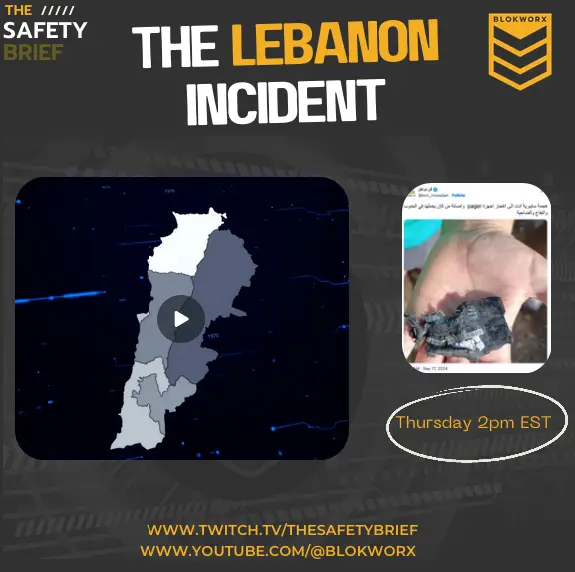
Recent cyberattacks on electronic devices have raised serious concerns about the security of personal devices and critical infrastructure alike. The recent Lebanon incident is a strong...
Many organizations require a multi-layered approach to cybersecurity in today’s digital age. BLOKWORX delivers just that with a suite of powerful services designed to cover every angle from endpoint...
In today’s rapidly changing cybersecurity landscape, technical defenses are only as effective as the culture that supports them. For organizations to stay secure, it’s crucial to cultivate a strong...
As cyber threats evolve, staying ahead requires more than just reactive measures. BLOKWORX’s Managed Advanced Endpoint Defense (MAED) + Endpoint Detection and Response (EDR) solution meets this...
As summer days wind down and the excitement of back-to-school season begins, there’s more to think about than just new supplies and classroom rules. In today’s digital age, ensuring our...