Ransomware Prevention: A Persistent Problem Top of Mind for The City of Dallas
Ransomware continues to be a pressing cybersecurity threat, causing significant disruptions and financial losses for individuals, businesses, and municipalities. The recent 2023 Dallas ransomware incident serves as a stark reminder of the devastating consequences of such attacks. This incident, not the first of its kind in Dallas, highlights the ever-present need for proactive cybersecurity strategies […]
Cybersecurity Tools: Is More Security Better Security?

Recently, we attended several industry events. Looking around the vendor halls, there were no less than 30 vendors providing cybersecurity tools. All of them presented value and hit different portions of the attack surface. We got to thinking, though, if we were an MSP, we would be completely overwhelmed with the number of options in […]
EvilExtractor: Awareness and Hygiene!

EvilExtractor malware extracts sensitive or confidential information from a victim’s computer system without their consent or knowledge. It falls under the category of information-stealing malware, which is a prevalent and dangerous type of cyber threat. EvilExtractor (also known as Evil Extractor) is marketed for sale for other cyber criminals to steal data and files for […]
Infamous Emotet is Back in Play
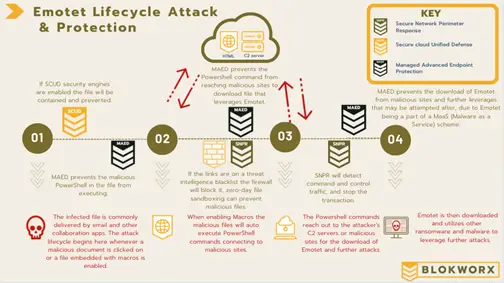
Emotet, a self-updating modular trojan horse malware, has again raised its ugly head. Emotet, also known as “The Banker,” was first discovered in 2014 as a banking Trojan. However, over the years, it has evolved into a multifunctional malware that is primarily distributed through spam emails, malicious attachments, and infected links. It is typically delivered […]
Third-Party Integrations – Productivity vs. Risk

Although a patch alleviates the threat, a vulnerability dubbed GhostToken reveals the danger of installing third-party integrations into sanctioned apps. GhostToken allowed attackers irrevocable access to an individual’s Google account using an authorized third-party application converted into a malicious trojan. Bad actors could hide in plain sight by removing the application from a Google user’s […]
Onboarding – A White Glove Experience

You’re investigating a new tool and it appears to solve all the problems you’ve been facing. The value justifies the cost, but you just can’t seem to pull the trigger. Why? You don’t have the time or the resource needed to dedicate to the onboarding effort, and we all know that onboarding is one of […]
EDR v. Threat Hunting v. Endpoint Protection
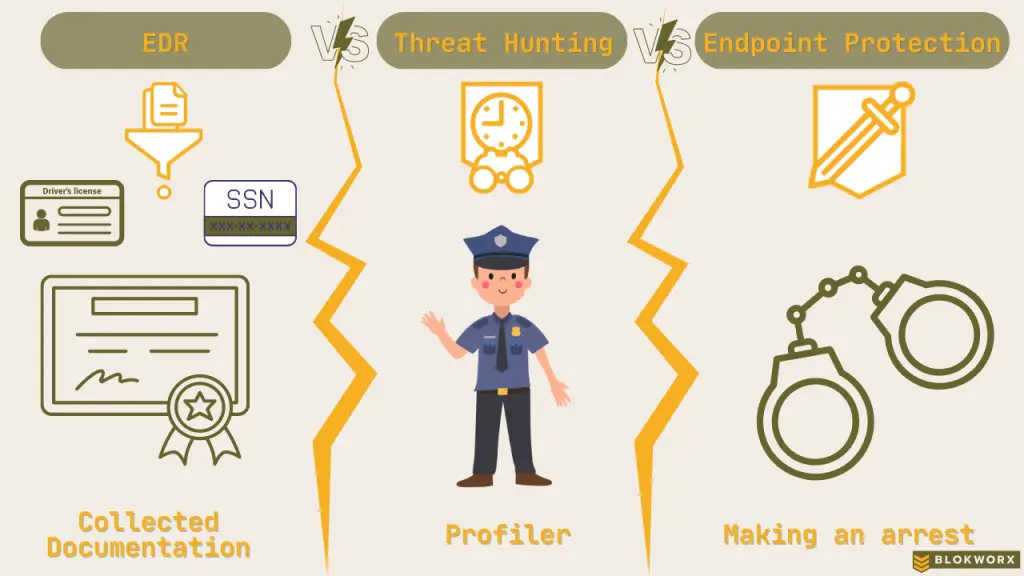
It seems like everyone you speak with has their favorite tool – EDR v. threat hunting v. endpoint protection. Unfortunately, this often leads to relying on one tool while ignoring the others, and other times conflating one tool’s capabilities into another. Realistically, EDR, threat hunting, and endpoint protection are all important for security. Why? Because […]
Is Your EDR Vulnerable?

Recently, cybersecurity experts reported that many EDRs are vulnerable to an attack that takes advantage of the “delete after reboot” command to maliciously wipe data. Endpoint security solutions traditionally use this feature to force a reboot and delete malicious files. Malicious actors have now weaponized the feature to delete important, and otherwise, uncompromised data. Even […]
Correlation, Causation, or Checking Boxes

“I need a SIEM. I need a SOAR.” These are requests we field everyday from MSPs. Our first question is always, “What are you looking to accomplish?” Unfortunately, the vast majority of the time the answer is, “I’m filling out an insurance form, and it says that in order to be eligible for cyber insurance, […]
IRaaS is a Step Backward for the Channel

Over two decades ago, the IT industry began to shift from break-fix to managed services. Savvy business owners on both sides of the equation recognized that it made a lot more sense to have predictable expenses dedicated to IT services rather than wait for something to break and rack up unknown costs fixing the issue. […]
Get on the YOLO Bus AKA Find Work-Life Balance

Friday, March 4, was the National Day of Unplugging. This begs the question, when did you last really unplug? Some companies took the day off Friday, as a mandatory day to relax; but we’re willing to bet you weren’t one of them. As an IT company, you’re required to be present 24/7/365. Unfortunately, this is […]
Top 3 Cybersecurity Mistakes MSPs Make
Working with MSPs every day, we see a lot of cybersecurity mistakes. In fact, preventing these mistakes is the whole reason for BLOKWORX existence. These are the top 3 cybersecurity mistakes we see MSPs make every day. 1. Paying for a Service and Not Fully Deploying It We recently got an escalated support ticket from […]
