BLOG
In today’s fast-paced digital world, the mental well-being of employees is more important than ever. Mental health issues such as stress, anxiety, and burnout can significantly impact an...
Compliance frameworks play a crucial role in addressing cybersecurity concerns within organizations. However, it is important to acknowledge their limitations. While these frameworks provide a...
As technology rapidly advances, artificial intelligence (AI) is at the forefront, changing how we live with personalized recommendations and virtual assistants. However, as AI becomes more...
Ransomware is still an ongoing nightmare and customers are being hit with it daily. Not all attacks will be high-profile but there will be countless attacks per week (successful attacks). As an...
What is the price when an app is free? We see this all the time, an application is free to use and promises no catches, but is it really free? The long and short is most commonly no, the app is not...
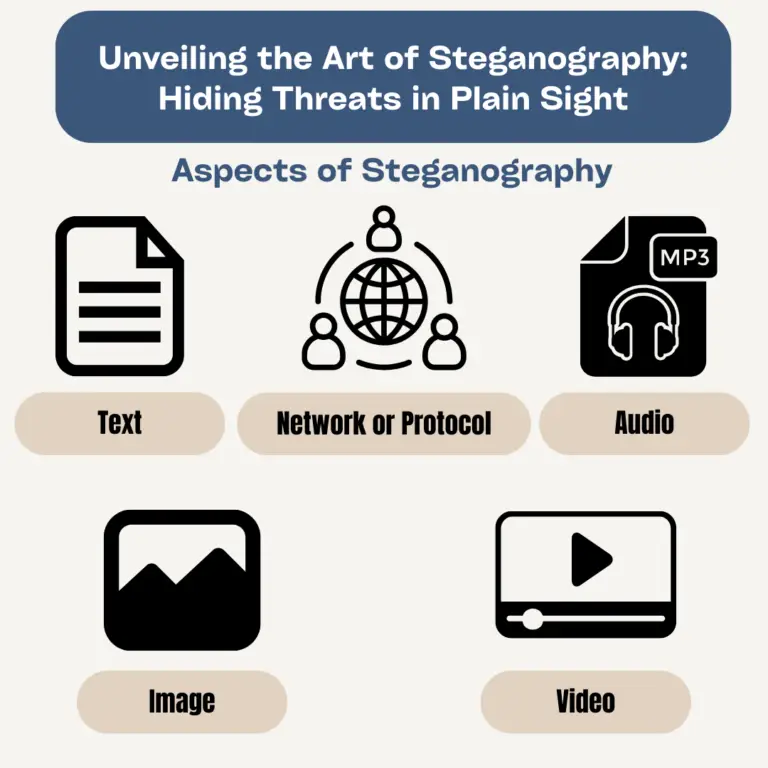
The art of hiding in plain sight is something most special agents strive for as it gives them the ability to slip in and out without drawing attention to themselves. Threat actors are doing the same...
Cybersecurity incidents have become an unfortunate reality for organizations of all sizes and industries. From data breaches to ransomware attacks, the results of these incidents can be severe...
In today’s cybersecurity landscape, just seeing threat alerts is not enough – you need to act fast. That’s where BLOKWORX comes in. While traditional tools provide visibility into cyber...
In both our personal and professional lives, the saying “You are who you surround yourself with” holds significant weight. This concept extends beyond human relationships into the realm of...