BLOG
In the dynamic landscape of cybersecurity, BLOKWORX is frequently approached by MSPs requesting either vulnerability scans or penetration tests. However, it’s crucial to distinguish between the...
As we bid farewell to 2023, we’d like to reflect on the major cyber-attacks that have shaped the digital landscape and set the stage for the upcoming year. Let’s dive into the notable...
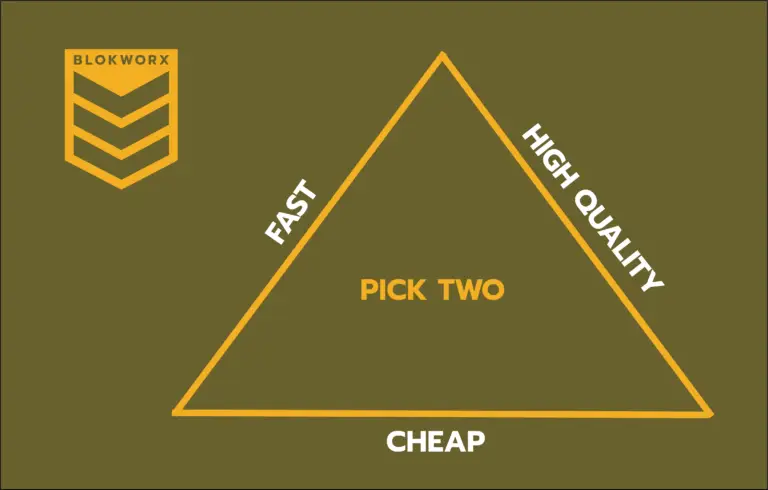
When dealing with products and product offerings you can place them in three buckets, commonly known as the triple constraint – Fast Cheap High Quality The kicker is that you can only pick two...
In a recent episode of The Safety Brief, we dove into the critical red flags in email, phone, and online behavior, equipping end users with the knowledge to defend against cyber threats. Let’s...
In the month of October, we observe Cyber Security Awareness Month—a vital occasion to reflect on the ever-present digital risks we encounter. Foremost among these is phishing, a widespread and...
October is the highlighted month for cybersecurity awareness, but it’s essential to remember that practicing good cyber hygiene should be a year-round commitment. In an increasingly digital...
In October, not just the vibrant hues of autumn deserve our attention. This month is designated as Cybersecurity Awareness Month, emphasizing the crucial need to safeguard our digital lives. Yet...
In the realm of cybersecurity, the ability to anticipate, adapt, and respond swiftly to threats is paramount. Much like the martial art of Jiu-Jitsu, which emphasizes leverage, strategy, and...
In the ever-evolving cybersecurity landscape, finding suitable candidates to defend against the constant barrage of cyber threats has become challenging. The issue perpetuates largely from employers...